2025年01月20日
Am I Being Observed Through My Smartphone by Someone?
We regard privacy as a critical concern. It involves several elements, including the websites and apps you access. Moreover, relatives may not fully comply with established restrictions.
Geolocation tools are not entirely detrimental; they can be advantageous when users provide their consent, such as in the case of finding a friend in a large gathering or seeking reassurance before a date. Nonetheless, their application can swiftly devolve into forms of cyber domestic violence.
We continue to assert that signal disruptors, particularly GPS blockers, represent the most effective strategy for countering tracking efforts. The feedback from our customers has been largely favorable in the past. By cutting off the GPS signal, these jammers prevent any data from reaching monitoring systems. Nevertheless, we understand that some customers may wish to reassess their choices before implementing a jammer.
Settings on iPhone
Apple permits the sharing of location details between Strawberry devices. If you wish to disable this functionality, you can do so by accessing Settings, then Privacy, and subsequently Location Services, where the Share My Location option is located. Once this option is turned off, a list of individuals with access to your GPS coordinates will be presented.
Spy App Cases
Tools such as SpyBubble and SpyPhone are characterized by their significant invasiveness. In addition to gathering location data, they can also extract confidential information, including the text of messages exchanged and the comprehensive list of calls made and received.
Some applications are especially hard to remove. In many cases, the only hint of their presence is a significantly accelerated battery discharge, although this phenomenon may also be associated with normal battery usage.
Utilizing specialized antivirus software for smartphones can effectively block threats or allow you to disable geolocation features on your device. For iPhone, access Settings > Privacy > Location Services, and for Android, go to Settings > Location. It is also advisable to check the settings of active applications. On iPhone, you can disable Background App Refresh by navigating to Settings > General. Android users should access Settings > Apps > Persistent to make similar adjustments. Be cautious, as these changes may affect the operation of other applications that rely on GPS data.
Your protected location data
An increasing number of websites and applications are tracking your location data more extensively than ever. Explore ways to ensure the security of your location information on your phone or computer.
Tips and tricks to protect your location data using the Internet
GhostPaint is an example of anti-tracking software that enhances online privacy. This tool features an easy-to-navigate dashboard that allows users to block various types of tracking software. It also educates users about the tracking services employed by the websites they visit. Although it is effective in preventing tracking from certain sites, it may not provide strong security measures or sufficient protection against location tracking, necessitating user awareness. Another useful software is Privacy Badger, which assists in preventing online surveillance. It detects websites that attempt to track user activities and remembers them to block future tracking attempts. While it is a valuable tool for privacy protection, it does not offer a high level of security.
Avoid Google Tracking
In many respects, Google can be considered synonymous with the internet. Every user of the internet interacts with Google in some manner. Those who utilize the internet for research, whether intentionally or not (it is worth noting that many of your favorite websites in your search bar are powered by Google), are subject to the search engine's various tracking methods. Have you noticed that when you click on a Google link or attempt to copy a link provided by Google, the resulting URL is often lengthy and convoluted, rather than simple? This complexity serves as a means for Google to track your data usage, as it seeks to gather extensive information from you and your connections. To avoid this tracking, consider employing straightforward add-ons such as SearchLinkFix.
Social Networking
Achieving true anonymity on the web in contemporary times necessitates the use of social media. For individuals who wish to access these platforms securely, it is vital to observe a specific rule: disclose minimal personal information regarding yourself and your location to prevent tracking. The location tracking feature is usually inactive unless intentionally enabled, but it is advisable to check its status. It is best to avoid this feature altogether and to mention your location exclusively in messages.
If you have executed all the steps mentioned earlier and still find yourself feeling unsafe, you have one final means of self-protection: a signal jammer. This device can effectively block the signals exchanged between the sender and the receiver. Why is this advantageous? Picture a scenario where an individual is tracking your location through GPS; by using a GPS jammer, you can prevent the GPS signal from reaching you, thereby disrupting the data flow between the tracking device and the system. This will ensure that you can no longer be tracked.
There exists a wide array of signal jammers available for purchase online, each designed for specific uses. For instance, the cell phone jammer is a device that can improve the signal strength of mobile phones. It is particularly useful in preventing unauthorized listening, which has led to an increase in the installation of such jammers in office environments to secure discussions during meetings. In addition, WiFi jammers are developed to disrupt WiFi signals, ensuring that internet connectivity is not accessible within their range.

2025年01月16日
Strategies for Avoiding Cell Phone Tracking
Is there a way to stop cell phone tracking? As location services depend on the hardware of your smartphone for accurate positioning, you can easily adjust these settings via the system preferences on both Android and iOS devices.
Preventing cell phone tracking: uninstall or turn off tracking software
If your phone has been lost or stolen, it is recommended to check its current location using a computer or tablet. This can be done through the built-in capabilities of the Android and iOS operating systems. For Android users, the "Find My Device" feature is available, while iOS users can find their device under "Find My iPhone" by entering their username and password.
In situations of emergency, the location details of your cell phone could potentially be exposed to hackers or spying entities. Therefore, it is recommended to turn off this feature in your smartphone settings or to ensure that your account is protected from unauthorized access.
There is a possibility that someone may purposefully install spy applications on your device. In this document, we will explain how to uninstall applications on Android and how to delete applications on iOS. Thus, if you come across an application that you did not install, it is wise to delete it as a safety measure, given that spy applications can often present themselves as other applications or mobile games.
Still not working?
In the event that the previously mentioned information fails to resolve your problem, you may be required to pay certain fees for a solution. GPS jammers are regarded as a final option for circumventing unwanted tracking. They operate similarly to noise generators, though it should be noted that they do not produce loud noises during their operation; they remain silent while emitting noise signals that disrupt GPS frequencies.
How to Know If Your Phone Has Been Hacked
Hackers are ever-present, but you can ensure the security of your data by being alert to signs of suspicious behavior. Here are some indicators that may suggest your phone has been hacked.
Data Quota Exhausted
In the event that you experience an unaccounted surge in your data usage, you might not be the only one accessing your data. A compromised iPhone or Android device has the potential to use your data for transmitting information acquired from your phone.
Slower than usual
A decline in performance is among the most frequent signs that your mobile device may have been hacked. If you notice that websites are taking an excessive amount of time to load or that applications are crashing unexpectedly, it may indicate that malware is monopolizing your phone's bandwidth or processing power. You might also experience issues with sending and receiving messages or with powering your device on and off.
Your phone is heating up
Is your device becoming excessively warm despite infrequent use? Engaging in lengthy activities like online movie streaming or prolonged gaming can elevate your phone's temperature. However, if this heating is not linked to your usage patterns, it may be due to other external factors.
Protect your phone with a jammer
Affirmatively, a signal jammer can contribute to your security by providing an extra layer of defense. This apparatus interferes with signals, rendering phone usage and internet access inoperative. If used properly, it can be advantageous.
At present, many organizations and companies are utilizing signal jammer
to address the potential threats of data leakage and eavesdropping. For instance, educational institutions have installed jammers to prevent students from accessing their phones during classes or exams. Gas stations have also adopted cell phone jammers to ensure that mobile devices are not used within their facilities. Recently, commercial organizations have begun to incorporate jammers in their offices, often turning them on prior to meetings to protect against unauthorized listening.
2025年01月15日
Be Vigilant About Unlawful Gps Surveillance
While GPS technology offers numerous advantages, it can also be misused quite easily. This misuse occurs when individuals are monitored without their consent in personal or professional settings. For instance, one may wish to track a partner's whereabouts when they are away from home or to observe employees during their breaks. Such covert surveillance is illegal, and anyone who tracks another individual without their awareness and permission infringes upon their personal rights, including those protected by the Federal Data Protection Act, potentially leading to administrative or criminal penalties.
GPS positioning via vehicle or mobile phone
GPS positioning can be achieved through either a vehicle or a mobile phone. A tracking device can be easily affixed to the vehicle, allowing for real-time location monitoring. This capability is especially beneficial for businesses operating a fleet of vehicles, as it streamlines the management of numerous daily operations. However, it is imperative that no personal movement data is gathered, as this would contravene local privacy regulations. Furthermore, employees must be notified and provide their consent when the vehicle they are using is subject to tracking.
GPS monitoring helps control employees
Monitoring employees through GPS during working hours or after they have clocked out is illegal without their knowledge and consent. If a company vehicle or mobile phone is located, this information should not be utilized to reach out to the employee directly. Activities during break times or after work hours are considered private matters and should not be interfered with. Should your supervisor engage in unauthorized surveillance of employees, they may be subject to reporting and appropriate penalties.
What you can do when someone is tracking you
The prevalence of GPS tracking appears to be unavoidable. If you find yourself under surveillance, do not assume that you are powerless to act. Utilizing GPS jammers may provide a solution to mitigate this issue.
GPS jammers function by obstructing GPS signals over a specified range, which may extend from a few meters to several kilometers. When a jammer is operational in a particular vicinity, GPS navigation devices and geolocation applications become inoperative. Consequently, GPS signals will be unable to reach your mobile device or vehicle, effectively removing you from their tracking capabilities.
It is important to understand that the removal of GPS signals will render all associated services, including your vehicle's navigation system, inoperative. Please take this into consideration prior to utilizing a jammer.
How to deal with illegal GPS tracking?
Using a GPS jammer
GPS jammers serve as essential devices for countering tracking efforts. They effectively obstruct GPS signals, thereby preventing any data transmission from your smartphone to the satellite.
It is essential to identify the specific GPS signal bands that require blocking. GPS frequencies span from L1 to L5; however, with Perfectjammer's advanced signal jammer, you can effectively block all frequencies using a single device. Additional options include desktop and portable devices, each offering varying coverage.
2025年01月07日
Legal Issues with Car Remote Control Jammers
Understand the functionality of car remote control jammers and the associated legal ramifications of utilizing such devices. While car remote control jammers can serve as a deterrent against theft, their deployment is subject to strict regulations in numerous areas due to the potential for disrupting legitimate communications and posing security threats. An examination of the legal considerations surrounding the use of car remote control jammers will provide insight into their legality across various jurisdictions and the legal constraints that users should be aware of to ensure compliance with the law.
Is it legal to use a car remote control jammer?
The legality surrounding car remote control jammers differs significantly across various nations. In certain jurisdictions, the use of these devices is strictly forbidden, whereas in others, regulations may be less stringent but still impose specific limitations on their application. It is essential for individuals contemplating the purchase or utilization of a car remote control jammer to familiarize themselves with the relevant local legislation.
In the United States, the regulation of car remote jammers is overseen by the Federal Communications Commission (FCC). The FCC enforces stringent rules concerning the use of jamming devices due to their potential to disrupt legitimate communications, including emergency services, GPS signals, and various wireless systems. Under the Communications Act of 1934, the use of any device that obstructs authorized communications or broadcasts is prohibited.
Legal Constraints: The utilization, distribution, or importation of car remote jammers is prohibited in the United States unless explicitly permitted by the FCC for designated professional or governmental applications. Violations of these regulations may result in significant fines and potential imprisonment.
The European Union maintains a stringent position regarding the utilization of jamming devices. The enforcement of regulations that ban the use of devices that interfere with radio signals falls under the jurisdiction of the European Telecommunications Standards Institute (ETSI) and the national regulatory authorities of its member states.
Legal Constraints: The deployment of car remote jammers is prohibited in the majority of EU member states due to their potential to interfere with essential communications and endanger public safety. In various nations, individuals apprehended for utilizing jammers may incur substantial fines or face criminal prosecution. Typically, the use of these devices is limited to official applications and is subject to stringent regulation.
Exceptions are present, similar to those in the United States, for certain professional applications, including those utilized by law enforcement or security personnel. Nevertheless, these exceptions are generally confined to specific situations and frequently necessitate special permits or licenses.
In the United Kingdom, the operation of car remote GPS blockers is prohibited by the Wireless Telegraphy Act 2006, which forbids any unauthorized transmission of radio signals. The regulation of wireless equipment, including jamming devices, falls under the jurisdiction of the Office of Communications (Ofcom).
Legal Constraints: The use of car remote jammers is deemed illegal unless they possess a license issued by Ofcom. Engaging in unauthorized operation of such a device may result in severe consequences, including monetary fines and the seizure of the equipment.
Exceptions to this rule generally pertain to governmental and law enforcement applications, which necessitate explicit authorization. Any individual or business attempting to utilize car remote jammers for personal use would be contravening UK law.
In Australia, the regulation of car remote jammers falls under the jurisdiction of the Australian Communications and Media Authority (ACMA), which is responsible for overseeing communication devices within the nation. As in many other areas, the use of jamming devices is strictly forbidden unless a specific license for authorized use has been obtained.
The utilization of car remote jammers is prohibited by Australian law, and individuals found using such devices without appropriate authorization may face fines and penalties.
Exceptions exist whereby, similar to other nations, law enforcement agencies may be authorized to utilize jamming technology for particular objectives; however, such instances are subject to stringent regulation.
In Canada, the operation of car remote jammers is prohibited by the Radiocommunication Act. The Canadian Radio-television and Telecommunications Commission (CRTC) is responsible for enforcing regulations concerning jamming devices, as they pose a potential threat to communication networks and public safety.
Legal Restrictions: In Canada, the unauthorized use of car remote jammers is strictly forbidden, and individuals found in violation may incur fines and have their devices confiscated.
Exceptions: In line with practices observed in other nations, law enforcement agencies may be authorized to utilize jamming devices under particular, regulated circumstances, such as in counter-terrorism operations or initiatives aimed at public safety; however, such usage necessitates formal approval.

2025年01月04日
The Impact of $50 Tin Box on Your Life
At this time, GPS satellite signals support your ability to reach out to your mother, energize your household, and ensure the successful landing of your aircraft; nevertheless, a budget-friendly plastic container can disrupt these essential operations.
Shortly after noon, San Diego, California, experienced a notable traffic disruption. Air traffic controllers at the airport tower noticed that the system used for tracking incoming aircraft was down. Simultaneously, the emergency pagers that alert medical staff at the Naval Medical Center also became inoperative. Additionally, the traffic management systems responsible for guiding ships failed, creating the potential for disorder at the busy port. On the streets, individuals attempted to use their cell phones, only to find no signal, and bank customers were unable to access cash from local ATMs. This problem persisted for an additional two hours.
The cause of the mysterious incident in January 2007 was determined after three days of investigation. At that time, two Navy ships were involved in training exercises at the Port of San Diego. Technicians, aiming to test the protocols for communication loss, jammed radio signals. This measure inadvertently disrupted the GPS satellite signals across a large section of the city.
The role of satellite signals has significantly broadened, extending well beyond the realm of your car's navigation system. GPS has emerged as an "invisible utility" that we frequently utilize without being fully aware of it. Cellular service providers depend on GPS time signals to facilitate communication between your phone and the network towers. Energy companies apply GPS technology to synchronize their grids when they are interconnected. Furthermore, financial institutions and stock exchanges utilize satellite data to generate timestamps, which are crucial for fraud prevention. Meanwhile, the reliance of society on GPS navigation continues to grow.
There is a growing apprehension among certain individuals regarding our reliance on technology that is vulnerable to failure, highlighting that significant disruptions can occur without the necessity of extreme military exercises. A significant concern revolves around GPS jammers—compact devices that can be affixed to a vehicle's dashboard. These devices are available for purchase online and are commonly used by individuals, such as truck drivers, who wish to obscure their locations from their employers. The increasing prevalence of these jammers has led to complications at airports and has caused cellphone signal failures in various metropolitan areas. When unobstructed, a jammer can interfere with GPS signals from several kilometers away. Thus, it is not surprising that researchers around the globe are working diligently to find solutions to prevent catastrophic GPS outages.
Stealth Utility
It is essential to recognize that when GPS systems fail, the consequences reach far beyond navigation. Donald Jewell, who has been instrumental in the development of GPS within the U.S. Air Force and is now the editor-in-chief of GPS World magazine, points out that our reliance on GPS is frequently unacknowledged. He estimates that there are over a billion GPS receivers in use today, with more than 90 percent depending on the signals primarily for their precise timing.
Cell phones are a primary application of this stealth capability. As users move, it is necessary for communication towers to align with one another to transfer calls, and GPS time signals present an affordable and precise means to accomplish this. The timing offset of each tower is also instrumental in its identification. In fact, many wireless communication technologies utilize GPS timing for synchronization purposes. This reliance likely led to the issues faced by traffic control and emergency pagers at the Port of San Diego in 2007.
Truck Cheating
Last intentionally designed a basic, commercially available jammers. While the use of such low-tech devices is illegal in the United States, the United Kingdom, and various other countries, they can be purchased online for as little as $30. Vendors claim that these devices are intended for privacy protection. Their ability to block devices that monitor a vehicle's movements has made them particularly popular among truck drivers who wish to avoid electronic surveillance in their cabs. Additionally, they can interfere with GPS-based toll systems that utilize onboard receivers. Some criminals employ these jammers to disable tracking devices in stolen cargo. "Initially, we thought the jammers might have been assembled in a bedroom by a young man with acne," states Last. "However, they are now being produced in factories in China."

2025年01月02日
There Is a Notable Increase in the Number of Caravan Thefts Occurring
A notable rise in caravan thefts has been observed across the nation recently, raising concerns. This increase is primarily driven by a shortage of vehicles and a growing demand for leisure vehicles. In September 2024 alone, several incidents were reported, reflecting this disturbing trend.
Police in North Yorkshire are currently investigating the theft of a Swift Elegance caravan from a location near the A63 in Selby. The caravan was reported stolen during the late night hours, and authorities are appealing for any witnesses or dashcam recordings that could help in their investigation.
In Scotland, a comparable situation arose when a Lunar Quasar caravan was stolen from a location in Radford, prompting the police to reach out to the community for any information related to the theft.
Police are recommending that caravan owners enhance their security strategies, with a specific emphasis on the installation of GPS tracking systems. These systems not only provide a greater opportunity for the rapid recovery of stolen caravans but are also essential in identifying the perpetrators behind the recent rise in thefts. A recent case in Lincolnshire highlighted this, where a man was arrested after authorities quickly located a stolen caravan on the A1. The caravan was found within 30 minutes of the theft, thanks to the GPS tracker affixed to it.
The current trend of thefts highlights the essential nature of being watchful and taking necessary precautions to protect your valuable leisure vehicles. Even if your caravan is equipped with a factory-fitted tracker, it is advisable to consider the installation of an additional hidden, battery-operated tracker, such as the Back2you Caravan Tracker. Professional thieves are often knowledgeable about the placement of factory-installed trackers and can easily remove them. Self-contained trackers can be discreetly hidden anywhere on the caravan, and their wireless design makes it extremely challenging for thieves to locate them.
GPS Jammers or GPS Blockers Stop Motorhome Recovery
Do They Work?
There is a chance that you have seen references to the employment of GPS interference devices by seasoned criminals or individuals who disapprove of their employers' intrusive monitoring.
GPS jammers are designed to emit a white noise radio signal that matches the frequency of GPS satellites, which can hinder the signals of GPS tracking devices and navigation systems. While these jammers or blockers are effective, their range is somewhat constrained.

2024年12月28日
Gsm Jammers for Vehicles
The introduction of GSM jammers for vehicles responds to the increasing necessity for privacy and security. These devices are specifically engineered to interfere with GSM signals, offering diverse applications such as minimizing distractions for drivers and bolstering safety during the transportation of sensitive items.
What are GSM Jammers for Vehicles?
A GSM Jammer for Vehicles functions as a device that disrupts GSM (Global System for Mobile Communications) signals. GSM is a standard that defines the second generation (2G) digital cellular network protocol employed by mobile phones. By blocking these signals, the jammer effectively prevents all GSM devices within its vicinity from engaging in calls, sending text messages, or utilizing data services.
How do GSM Jammers for Vehicles Work?
A GSM jammers for Vehicles functions on a relatively uncomplicated principle: it broadcasts radio frequencies akin to those employed by mobile phones, but with greater power. This produces "noise" that effectively masks the genuine signal from the cell tower. The jammer is specifically calibrated to the GSM operating band, which inhibits any communication between the phone and its cellular network.
In particular delicate situations, individuals may resort to using a GSM jammer to maintain their privacy or to prevent tracking through their mobile devices. Furthermore, certain commercial fleet operators implement vehicle gps blocker for car to keep drivers focused on the road, thereby reducing the likelihood of distractions from phone calls or text messages. In critical safety scenarios, such as the movement of VIPs or valuable assets, GSM jammers can be utilized to obstruct the remote triggering of explosive devices that are activated by cell phones.
Choosing the Right In-Vehicle GSM Jammer
When choosing an in-vehicle GSM jammer, consider the following factors:
- Coverage: Make sure the jammer covers the range you need and does not exceed that range to avoid causing unnecessary interference to other devices.
- Frequency Range: Choose a jammer that can block specific frequencies used by the devices you want to disrupt.
- Power Consumption: Consider how the jammer will affect your vehicle's battery life and ensure it does not consume excessive amounts of power.
Although the primary function of an in-vehicle GSM jammer is to bolster privacy or security, it is crucial to evaluate its possible repercussions on safety. A jammer, for instance, might interfere with communication during critical situations, thereby jeopardizing lives. It is imperative for users to understand these implications and devise strategies to alleviate any negative outcomes.

2024年12月27日
The Immediate Demand for an Effective National System to Detect Gps Jamming
GPS threats are increasing at a record rate
The escalation of conflicts worldwide is negatively impacting the reliability of GPS technology, with a notable increase in interference attacks disrupting large areas in Europe and the Middle East, resulting in serious inconveniences for civilians. Simultaneously, there is a rising trend of criminal elements employing jammers for drug trafficking, cargo theft, and various other illegal activities in North America. Recent years have seen sporadic GPS jamming and spoofing incidents that have affected major airports across the United States. Additionally, many American citizens are now purchasing affordable retail jammers, motivated by privacy concerns and the spread of anti-government conspiracy theories.
For years, security analysts have been alerting stakeholders to the dangers posed by targeted attacks on GPS, which could lead to disruptions in the financial system, power grid, air traffic management, and emergency response services. While there is a rising consensus on the necessity of developing alternative capabilities for GPS, it is imperative to also consider another vital issue that warrants focus.
There is an urgent necessity for America to establish an automated national detection system that can detect GPS interference instantaneously and generate accurate real-time maps showing the areas affected.
A critical weakness in our satellite navigation capabilities is the lack of a coordinated, real-time system for detecting high-precision jamming and spoofing, which exposes American government, commercial, and emergency operations to vulnerabilities within the nation.
Tracking emitters
Determining the exact source of an interference attack, namely the emitter, is vital for executing prompt and efficient countermeasures, such as disabling the jammer to restore navigation capabilities.
Locating the emitter facilitates the identification of the specific area where interference is taking place, indicating where the effects are likely to be most pronounced and which assets are at the highest risk.
Nonetheless, accurately identifying emitters using standard ground-based sensors presents significant difficulties. One primary obstacle is that mobile jammers often emit low-power signals, which are harder to detect from a distance and can reflect off surfaces like buildings, cars, and trees. Furthermore, the mobility of jammers, which frequently change their locations, adds another layer of complexity to tracking them. Moreover, sophisticated jammers may implement detection countermeasures, including omnidirectional antennas and frequency hopping, which further impede triangulation.
Implementing a smartphone-based detection system would greatly augment the number of sensors available for tracking the emitter. A closely-knit array of detection points would enable quicker and more accurate detection, confirmation, and aggregation of information concerning signal location in real time, regardless of any changes in the emitter's position. It has been established that large-scale networks of mobile devices can effectively monitor the ionosphere in real time, enhancing positioning accuracy.
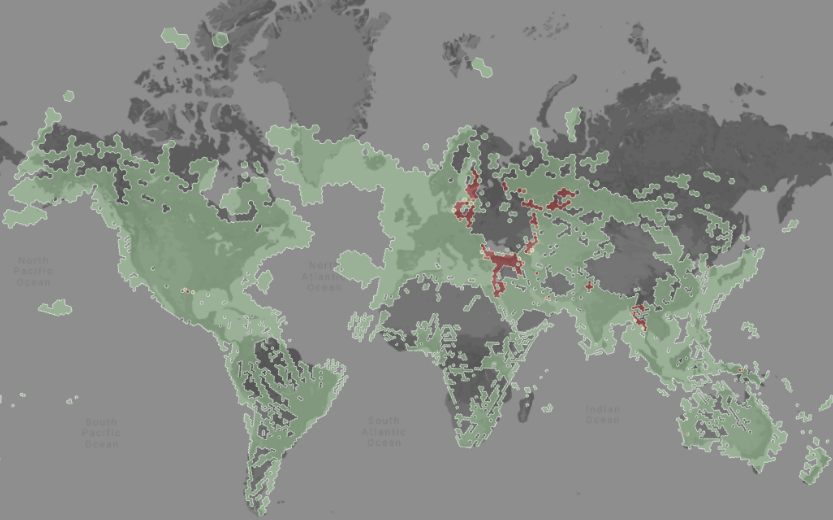
2024年11月21日
GPS Jammers Can Wreak Havoc, Cover up Crime
Comparable in prevalence to electricity, the Global Positioning System (GPS) has evolved beyond a simple convenience for travelers. It now plays a critical role in landing airplanes, navigating ships, coordinating data on communication networks, and managing the complexities of large power grids.
The precision in positioning and timing provided by GPS has led to a significant dependency, causing us to often underestimate its importance and assume its availability whenever we need it.
Initially, GPS was created for the purpose of tracking military equipment and vehicles, and it was not foreseen to be utilized in numerous civilian contexts. Recent occurrences have demonstrated that GPS is susceptible to security risks that could cause significant disruption to both personal devices and vital national infrastructure.
Small Cost, Big Consequence
The primary threat originates from a phenomenon that authorities are increasingly apprehensive about, namely the rising trend of utilizing low-cost GPS jammers.
Available for personal use at a minimum cost of $30, GPS jammers, also known as "anti-GPS" devices, can be quite small. Some versions are designed to look like a 12-volt car cigarette lighter power adapter that is linked to an antenna.
Online, these gadgets are advertised as means to enhance personal privacy and obstruct tracking of individuals' locations. However, reports from the UK indicate that such devices have also been misused by criminals and car thieves to mask their unlawful activities.
"The production of these items by Chinese factories is a cause for concern," remarked Peter Large, vice president of Trimble, a company located in Sunnyvale, California that focuses on advanced positioning systems. He warned that if these products become widespread, the impact could be severe.
The operation of GPS jammers involves the interference of frequencies within one of the standard GPS bands. Due to the inherently low power of GPS signals, which transmit at merely 25 watts from satellites situated around 12,500 miles above the Earth, these signals can be easily disrupted or interfered with by receivers, including portable navigation devices.
Due to the common practice of equipping vehicles with onboard GPS receivers by car and truck fleet operators, some drivers resort to using signal jammers to hinder their supervisors from tracking their movements.
According to a November report from the government-established National Positioning, Navigation and Timing (PNT) Advisory Commission, "Our current capabilities to detect and counter GPS jammers are inadequate." The report highlighted that "It took an extended period to identify the device that was interfering with the new GPS landing system at Newark Airport in New Jersey."
GPS signals are set to serve as the foundation for the forthcoming generation of air traffic control systems that oversee aircraft in flight, moving away from the existing system that depends on radar and human intervention.
In addition to overseeing road and marine traffic and managing data and power networks, GPS signals are instrumental in regulating traffic light timings and guaranteeing that automated farming equipment performs accurate plowing and harvesting of fields.
Interfering with any of these systems may lead to severe consequences.
According to Trimble's Large, there is a significant concern that GPS jammers could serve as a weapon.
The National PNT Advisory Commission's report concurred on the necessity of enhancing GPS systems employed in national security operations, such as those in fighter jets and other military technologies, to withstand threats. It also designated GPS as essential infrastructure.
The urgent development and deployment of systems that can efficiently detect, counteract, and deactivate jammers is essential. Additionally, there is a critical need for laws that grant the authority to apprehend and prosecute those who intentionally commit such offenses.
This month, the Royal Academy of Engineering in the UK published a report that reached analogous conclusions.
According to the report, global navigation satellite services (GNSS) have reached a level of convenience and prevalence that users frequently take them for granted. It emphasizes that while the failure of these services in a particular application may only result in minor inconveniences, a more extensive failure affecting multiple systems could have far-reaching and serious implications.
In the United States, GPS jammers are deemed illegal, and similar restrictions apply in numerous European countries. However, the legal framework in some other nations is not as well-defined.

2024年11月18日
Investigating GPS Jamming Technology
The Global Positioning System has become a vital component of today's world, offering accurate positioning, navigation, and timing information for numerous applications. GPS is integral to various industries, aiding in daily commutes as well as in executing precise military operations. However, the increasing use of advanced technologies designed to block GPS signals has led to a corresponding rise in the threat of signal disruption.
The term modern gps jammers denotes a technology that deliberately interferes with signals, causing receivers to be unable to precisely identify their location or acquire reliable timing information. This disruptive technology carries substantial risks in both civilian and military contexts, potentially leading to safety hazards, disruptions in operational GPS signals, and economic losses.
This detailed guide will investigate the nuances of blocking technology, seeking to offer a more profound comprehension of its implications, detection techniques, and mitigation approaches. Through an analysis of the core principles, diverse categories of GPS interference devices, and their potential impacts, we can gather significant insights into this escalating concern.
Furthermore, we will assess the actions taken to identify and combat jamming, including the creation of anti-jamming technologies and the establishment of regulatory policies. Additionally, we will review current countermeasures and deliberate on prospective trends in managing this continually evolving threat landscape.
It is crucial to comprehend jamming technology to protect the reliability and security of essential systems reliant on GPS. Through increased awareness and collaborative efforts, we can develop robust strategies to address the threats posed by jamming, ensuring the continuous operation of GPS-dependent applications in various industries.
We encourage you to participate in our endeavor to investigate the complexities associated with jamming technology, analyze its implications, and review the actions taken to address this perpetually evolving challenge.
Do GPS jammers exist: work principles
The Global Positioning System, commonly known as GPS, is a satellite-driven navigation system that offers users accurate information regarding positioning, navigation, and timing on a global scale. It functions by utilizing satellites and overseeing ground stations and receivers to identify specific geographic locations.
What does GPS jamming do: technology explained
Distinct classifications of GPS jamming devices involve intentional interference methods aimed at disrupting the normal functionality of GPS receivers. By broadcasting robust signals within the designated GPS jamming frequency bands, these signal jammers can overpower or obstruct weaker signals, complicating or rendering impossible the receivers' ability to secure accurate positioning, navigation, or timing information.
Here are vital aspects to understand about blocking:
- Purpose of GPS Jamming: The primary purpose of jamming is to create GPS signal disruption methods. It can be employed for various reasons, including criminal activities, privacy concerns, military operations, or unauthorized actions to undermine the functionality of devices or services.
- Types: GPS jammers come in various forms and sizes, ranging from small handheld devices to more powerful stationary or vehicle-mounted systems. Portable jammers can affect localized signals, while larger ones can cover broader regions.
- Working Principles: GPS jamming device operation transmit radio frequency (RF) signals in the same frequency bands. The jamming signals overpower or interfere with the weaker signals, disrupting GPS tracking signals. This interference prevents accurate positioning, navigation, or timing calculations.
- Impact: Jamming can have significant consequences in different sectors. In civilian applications, it can disrupt navigation systems, affect logistics GPS jammer circuitry and operation, compromise emergency services, and impact industries reliant on precise timing, such as telecommunications and power grids. Jamming can hinder military operations, compromise situational awareness, and disrupt communication systems in military scenarios.
- Detection and Mitigation: Detecting blocking incidents can be challenging since jammers often operate covertly. However, various techniques to block GPS signals are employed to identify jamming signals, including RF monitoring, geolocation techniques, and anomaly detection algorithms. To mitigate the effects of jamming, anti-jamming technologies, such as adaptive antenna arrays and receiver algorithms, enhance receiver resilience against jamming attacks.
- Regulatory Measures: Many countries have regulations to prohibit the sale, possession, or use of jammers due to their potential negative impact. Jamming signals is illegal in most jurisdictions, and offenders can face severe penalties.
- Future Trends: As the technology behind GPS interference continues to evolve. Consequently, research and development efforts are focused on developing more robust anti-jamming solutions, advanced detection techniques, and enhancing security and resilience.








